Security researchers have uncovered a new malware toolkit known as Stanley, sold on Russian cybercrime forums, that uses malicious browser extensions to silently redirect users to phishing websites while keeping the legitimate URL visible in the address bar.
The malware is marketed as a premium toolkit, priced between $2,000 and $6,000, and is advertised as capable of bypassing Google Chrome Web Store moderation.
How the Stanley Malware Works
Unlike traditional phishing attacks, Stanley operates through a browser extension that injects malicious content directly into legitimate websites.
This technique allows attackers to present fake login forms or payment pages while the browser continues to display the correct domain name, making the attack extremely difficult for users to detect.
Underground Marketplace Listing
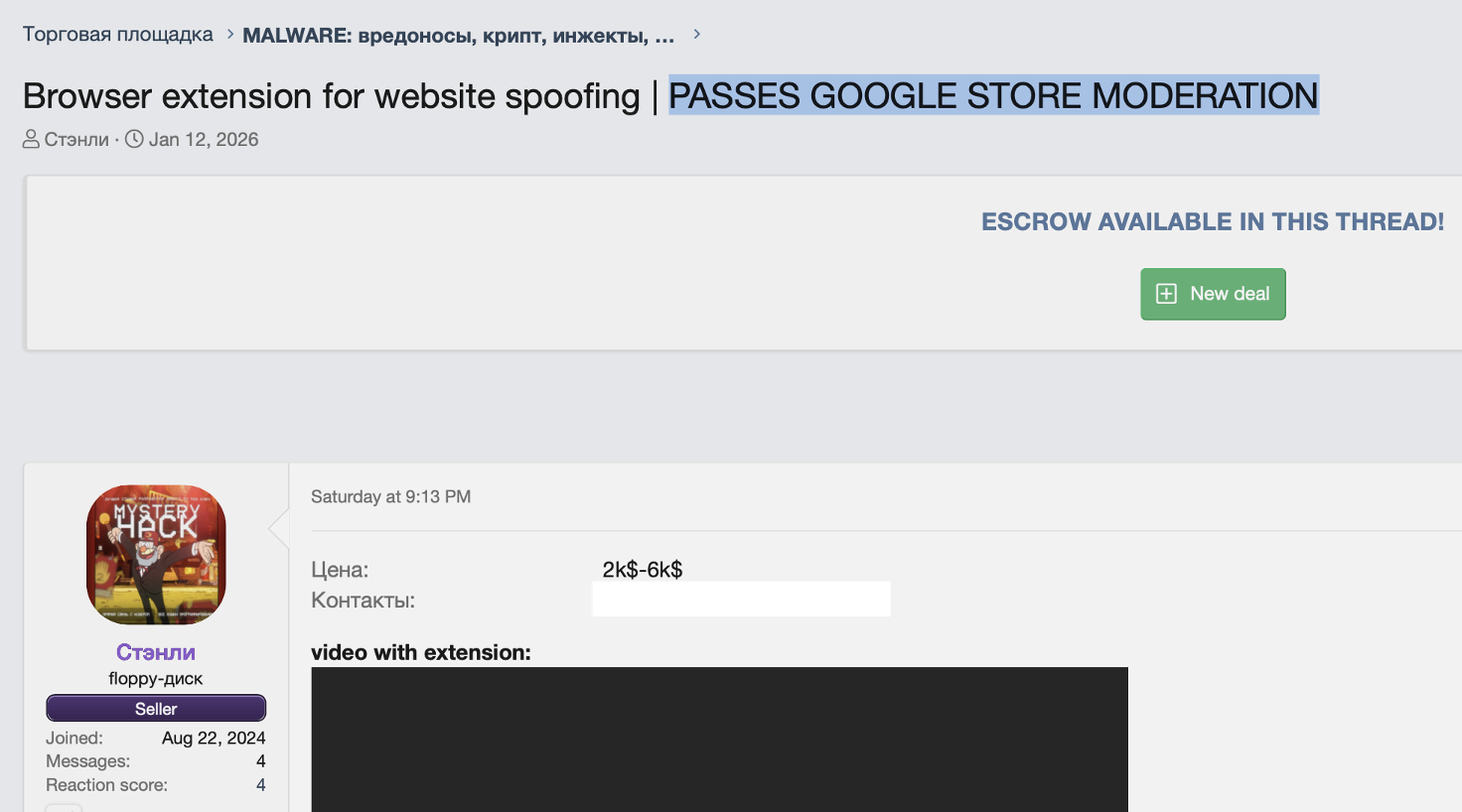
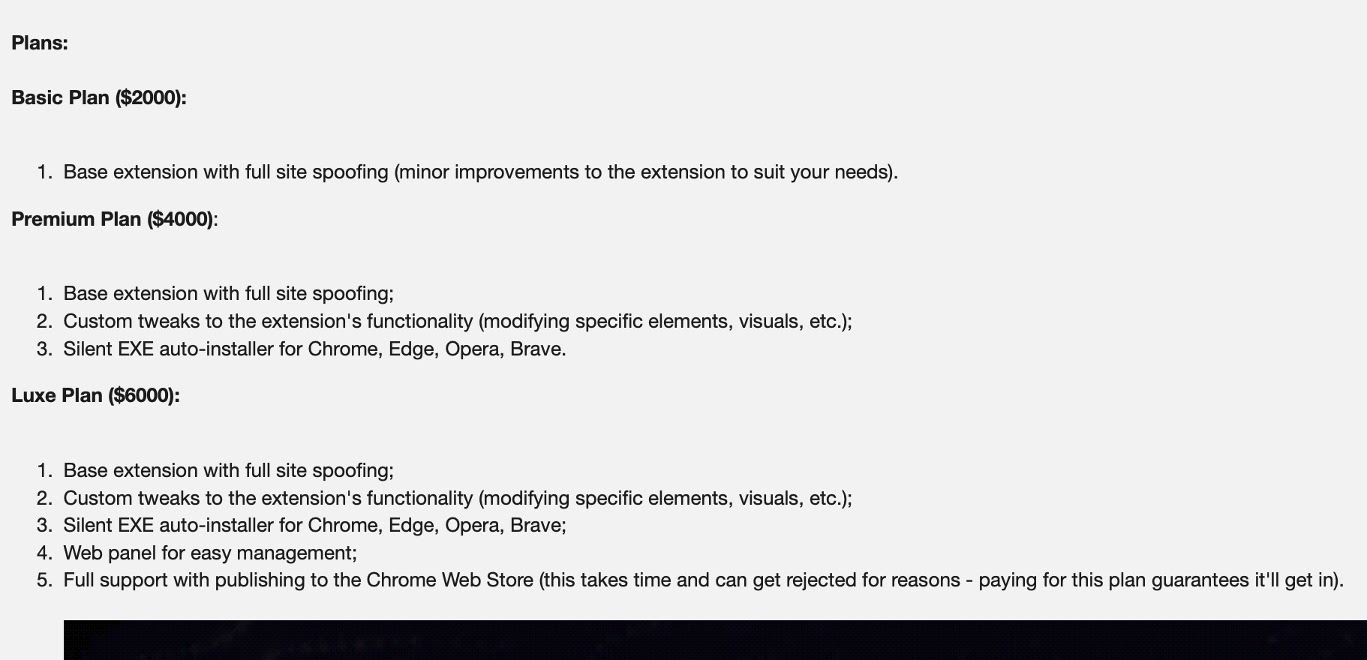
The toolkit is actively promoted on underground marketplaces, with sellers claiming escrow support, frequent updates, and compatibility with Chrome-based browsers.
Malicious Extension in Action
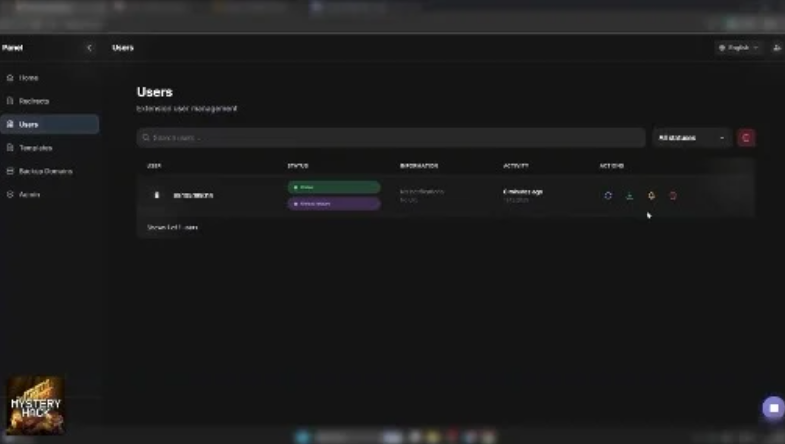
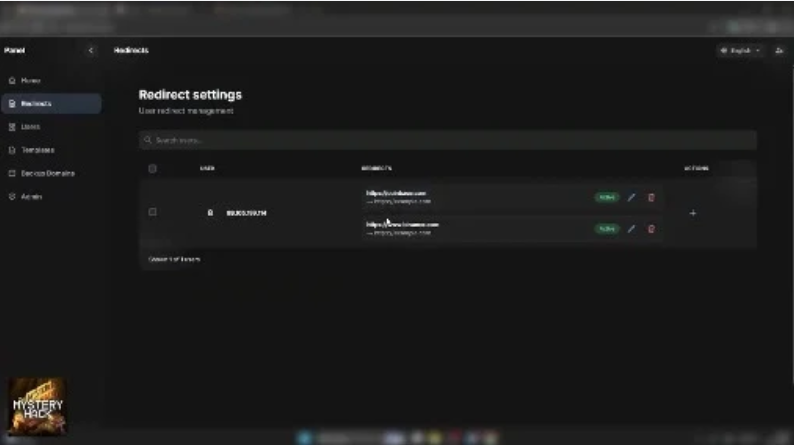
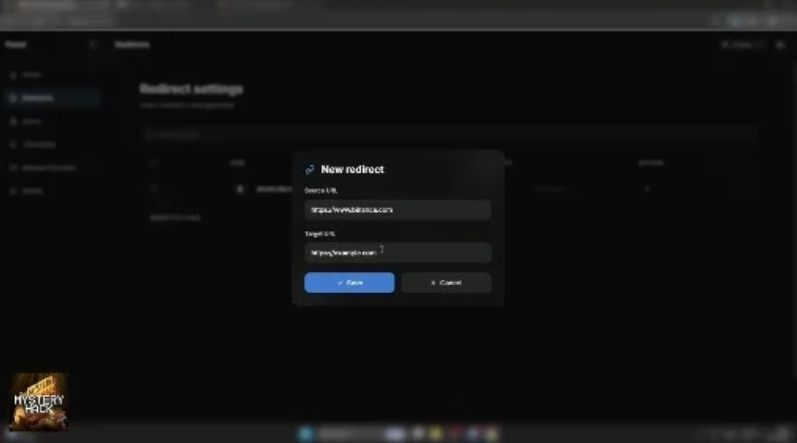
Once installed, the extension can selectively target banking portals, cryptocurrency services, email providers, and enterprise login pages, harvesting credentials and sensitive data in real time.
Why This Attack Is Dangerous
- Legitimate URLs remain unchanged in the address bar
- No obvious redirects or pop-ups
- Bypasses traditional phishing detection
- Abuses trust in browser extension ecosystems
What Users Should Do
- Remove unnecessary browser extensions immediately
- Install extensions only from trusted developers
- Audit extension permissions regularly
- Use hardware security keys or passkeys when possible
Sources & References
- Varonis — Stanley: A $6,000 Russian Malware Toolkit
- CyberSecurityNews — New Malware Toolkit Sends Users to Malicious Sites
This article was written for DigitalEscapeTools based on independent security research and publicly available threat intelligence.



